Picus Red Report 2026 Finds 38% Drop in Ransomware Attacks as Hackers Choose "Silent Residency&
Analysis of more than 1.1 million malicious files and 15.5 million adversarial actions across enterprise environments shows attackers are prioritizing long-term access through evasion, identity abuse, and misuse of trusted systems
SAN FRANCISCO, Feb. 10, 2026 (GLOBE NEWSWIRE) -- Picus Security, the leading security validation company, today released the Red Report™ 2026, revealing a chilling evolution in cyber warfare: the rise of the "Digital Parasite." Analyzing over 1.1 million malicious files and 15.5 million actions in 2025, Picus Labs found that adversaries have shifted 80% of their tradecraft toward stealth, evasion, and persistence.

The report uncovers distinct, highly sophisticated behaviors that allow malware to inhabit systems for months without detection:
- Malware Doing Math: In a first-of-its-kind finding, malware strains like LummaC2 are now using trigonometry (calculating Euclidean distance of mouse angles) to distinguish between human users and automated security sandboxes. If the mouse moves too "perfectly," the malware knows it is being watched and refuses to detonate.
- The "Play Dead" Phenomenon: Virtualization/Sandbox Evasion has surged to become the #4 most prevalent technique. Modern malware actively checks for analysis environments and goes dormant to create a false sense of safety.
- The Shift From Encryption to Extortion: The use of "Data Encrypted for Impact" (ransomware's signature move) dropped by 38%. Attackers are no longer locking data immediately; they are silently exfiltrating it for extortion
“We forced the adversary to evolve,” said Dr. Süleyman Özarslan, co-founder and VP of Picus Labs. “As organizations mastered backups and resilience, the traditional business model collapsed. Attackers no longer need to lock your data to monetize it; they just need to steal it. This is why we see a 38% drop in encryption and a staggering 80% surge in evasion techniques.”
Stealth and persistence dominate attacker techniques
The Red Report™ 2026 is based on year-long research conducted by Picus Labs, with adversarial behaviors validated through real-world attack simulations and mapped to the MITRE ATT&CK framework. The analysis focuses on the techniques attackers use most frequently to maintain access and avoid detection once inside an organization.
Among the report’s key findings:
- Process Injection Is King: For the third consecutive year, process injection (30%) is the top technique, allowing attackers to hide malicious code inside legitimate, trusted applications.
- Physical Insider Threats: State-sponsored actors (specifically DPRK operatives) are now utilizing physical IP-KVM devices to bypass software agents entirely, controlling laptop farms at the hardware level.
- Living Off the Cloud: Attackers are routing command-and-control (C2) traffic through high-reputation services like OpenAI and AWS to blend in with normal business traffic.
- Identity is the New Perimeter: one in four attacks now involve stealing saved passwords from browsers, allowing adversaries to authenticate as valid users.
By operating through trusted processes and standard network traffic, adversaries reduce their operational footprint and extend dwell time. Attackers can persist within environments while minimizing signals that would typically trigger alerts or responses, inflicting maximum damage.
Protecting enterprises from digital parasites
The Red Report™ 2026 concludes that static assessments and assumption-based coverage leave blind spots when threats are designed to remain quiet. Protecting enterprises requires continuous validation of security controls against real adversary behavior.
By validating defenses through ongoing attack simulation, organizations can confirm whether detection and prevention controls are effective against stealth-driven techniques and identify gaps before attackers exploit them.
The Red Report™ 2026 is available now. To download the full report and explore the most prevalent attacker techniques shaping today’s threat landscape, visit the Picus Security website.
Note on Methodology: The findings in the Red Report 2026 are derived from a large-scale analysis of 1,153,683 unique files (94% classified as malicious) and 15.5 million malicious actions collected by Picus Labs between January and December 2025. These actions were systematically mapped to the MITRE ATT&CK® framework to identify the most prevalent adversary techniques.
About Picus Security
Picus Security, the leading security validation company, gives organizations a clear picture of their cyber risk based on business context. Picus transforms security practices by correlating, prioritizing and validating exposures across siloed findings so teams can focus on critical gaps and high-impact fixes. With Picus, security teams can quickly take action with one-click mitigations to stop more threats with less effort. Offering Adversarial Exposure Validation with Breach and Attack Simulation and Automated Penetration Testing, working together for greater outcomes, Picus delivers award-winning, threat-centric technology that allows teams to pinpoint fixes worth pursuing.
Follow Picus Security on X and LinkedIn.
Media Contact
Jennifer Tanner
Look Left Marketing
picus@lookleftmarketing.com
Photos accompanying this announcement are available at:
https://www.globenewswire.com/NewsRoom/AttachmentNg/bc024cfe-e10d-4875-9f5b-6ccc7d1773b5
https://www.globenewswire.com/NewsRoom/AttachmentNg/2608d306-0ac9-4f37-9b23-8bbdeefc386c
https://www.globenewswire.com/NewsRoom/AttachmentNg/f227fb5b-832a-4b7e-99cd-ba0e0e9c11dc
- Urgent Call for Federal Investigation Into Town of Palm Beach Police: McWhorter Foundation Request
- Philips announces exchange ratio for 2024 dividend
- 蒋一侨《乘风2025》三公小考《跳楼机》震撼全场 全开麦舞台魅力十足
- Tulip Innovation推出基于LG Energy Solution和Panasonic Energy锂离子电池技术的新专利许可计划
- 中广欧特斯实力助阵传统养殖业用上“空气能”,成本直降60%
- 吕文平博士拆解工业AI落地:全应科技IDIC工具,破解智能化“纸上谈兵”困局
- 急性扁桃体炎与裸花紫珠胶囊:科学防治的全面解读
- “互联网+”助力青脆李产业数字化升级!
- 激光雷达头部企业图达通港股上市,首日大涨33%
- 收入狂飙同比增长137% 多款产品蓄势以待 康希诺增长动能充沛
- 2025新年启航!中韩合资·利多齿迪拜国际口腔展圆满举办
- 首秀炸场CCR!东软医疗这3款硬核新品凭什么?
- YY Group Announces Closing of $4 Million Registered Direct Offering
- 持续领跑!国产血液净化品牌再创新高
- 4.24亿!神州控股科捷中标中国移动全国物流项目
- 宁德时代发布骁遥双核电池,推出颠覆式动力电池解决方案
- 笃行女性关怀!恒昌医药联合创始人叶虹当选金霞经开区妇联副主席
- 华为智选与空净十大品牌IAM,携手共建数据驱动健康生活新范式
- 字节跳动携手Tecnotree Moments推动下一代人工智能和5G电信企业的变现
- 湘潭生态农业:绿色生态,绘制乡村振兴新画卷
- 牡丹中国芯 聚力赢未来——2026花皙蔻KA连锁系统领袖峰会圆满落幕,战略赋能启新程
- 用速度与温度守护——中国人寿财险全力应对强对流天气
- 联合推新,浪味仙×虎邦辣酱解锁辣味新成就
- Andersen Global与Celen在土耳其签署合作协议
- 海运订舱为什么要找货代?咱自己直接去找船公司订舱不可以吗?
- 葫芦娃药业集团党委书记、董事长刘景萍荣膺“2024年度十大影响力人物” 彰显行业领军风范
- WEEX唯客反诈实战手册:识别伪装套路,守护资产安全
- 万里长征映初心,红土蝶变焕新颜
- “互联网+”助力新媒体升级,义乌网激活行业新动能!
- 年货进京1号线 有“蛇”有得新年见——热烈庆祝俸山文旅发展有限公司入选北京地铁1号线年货进京专列
推荐
-
 透过数据看城乡居民医保“含金量” 缴费标准是否合理?
记者从国家医保局了解到,近期,全国大部分地区
资讯
透过数据看城乡居民医保“含金量” 缴费标准是否合理?
记者从国家医保局了解到,近期,全国大部分地区
资讯
-
 男子“机闹”后航班取消,同机旅客准备集体起诉
1月4日,一男子大闹飞机致航班取消的新闻登上
资讯
男子“机闹”后航班取消,同机旅客准备集体起诉
1月4日,一男子大闹飞机致航班取消的新闻登上
资讯
-
 王自如被强制执行3383万
据中国执行信息公开网消息,近期,王自如新增一
资讯
王自如被强制执行3383万
据中国执行信息公开网消息,近期,王自如新增一
资讯
-
 新增供热能力3200万平方米 新疆最大热电联产项目开工
昨天(26日),新疆最大的热电联产项目—&md
资讯
新增供热能力3200万平方米 新疆最大热电联产项目开工
昨天(26日),新疆最大的热电联产项目—&md
资讯
-
 一个“江浙沪人家的孩子已经不卷学习了”的新闻引发议论纷纷
星标★
来源:桌子的生活观(ID:zzdshg)
没
资讯
一个“江浙沪人家的孩子已经不卷学习了”的新闻引发议论纷纷
星标★
来源:桌子的生活观(ID:zzdshg)
没
资讯
-
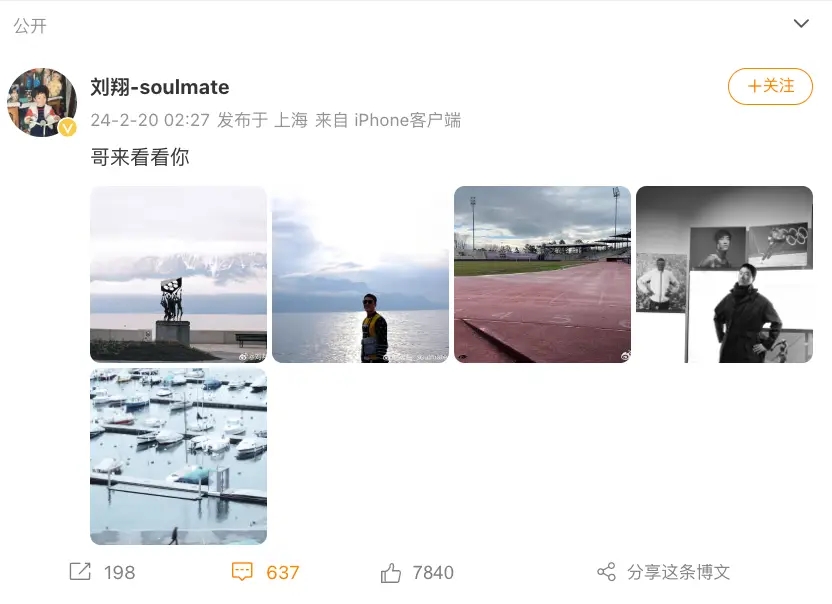 奥运冠军刘翔更新社交账号晒出近照 时隔473天更新动态!
2月20日凌晨2点,奥运冠军刘翔更新社交账号晒
资讯
奥运冠军刘翔更新社交账号晒出近照 时隔473天更新动态!
2月20日凌晨2点,奥运冠军刘翔更新社交账号晒
资讯
-
 国足13次出战亚洲杯首次小组赛0进球
北京时间1月23日消息,2023亚洲杯小组
资讯
国足13次出战亚洲杯首次小组赛0进球
北京时间1月23日消息,2023亚洲杯小组
资讯
-
 大家一起关注新疆乌什7.1级地震救援见闻
看到热气腾腾的抓饭马上就要出锅、村里大家
资讯
大家一起关注新疆乌什7.1级地震救援见闻
看到热气腾腾的抓饭马上就要出锅、村里大家
资讯
-
 看新东方创始人俞敏洪如何回应董宇辉新号分流的?
(来源:中国证券报)
东方甄选净利润大幅下滑
资讯
看新东方创始人俞敏洪如何回应董宇辉新号分流的?
(来源:中国证券报)
东方甄选净利润大幅下滑
资讯
-
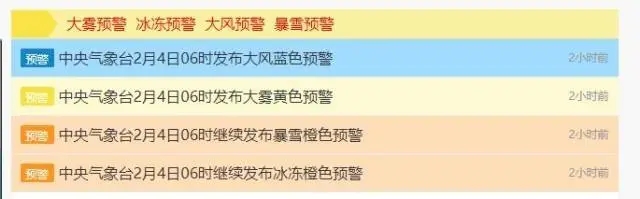 中央气象台连发四则气象灾害预警
暴雪橙色预警+冰冻橙色预警+大雾黄色预警+
资讯
中央气象台连发四则气象灾害预警
暴雪橙色预警+冰冻橙色预警+大雾黄色预警+
资讯


